COMP 3000 2011 Report: Damn Vulnerable Linux: Difference between revisions
No edit summary |
|||
| Line 24: | Line 24: | ||
==Installation / Startup== | ==Installation / Startup== | ||
To install Damn Vulnerable Linux, make sure to obtan the most recent ISO file from Sourceforge.[6] | |||
===VMware Player Settings=== | |||
[[File:DSL_img1.jpg|thumb|right|'''Figure 1: '''VMware Guest OS Settings]] | |||
<ol> | |||
<li>Using VMware Player, Create a new virtual machine. | |||
<li>Choose the option to install from disc image file, and browse to find the ISO location on your machine. | |||
<li>When VMware prompts for the guest operating system, select ‘Linux’ and then ‘Other Linux 2.4.x kernel’ before proceeding. | |||
<li>When naming the virtual machine, enter ‘DVL’ and select next. | |||
<li>The default disk capacity and hardware settings are sufficient, so proceed through these stages without making any changes. Click Finish. | |||
<li>Click enter to boot the system. | |||
<li>After the system successfully boots, login as ‘root’ with password ‘toor’. | |||
<li>To switch from the command line to a graphical interface, type ‘startx’. | |||
</ol> | |||
[[File:DSL_img2.jpg|thumb|left|'''Figure 2: '''Login Screen After Successful Boot]] | |||
[[File:DSL_img3.jpg|thumb|'''Figure 3: '''Starting The GUI Alternative]] | |||
==Basic Operation== | ==Basic Operation== | ||
==Usage Evaluation== | ==Usage Evaluation== | ||
Revision as of 15:57, 16 October 2011
Part I
Background
Damn Vulnerable Linux (DVL) is a Slax-based, live-DVD Linux distribution designed as a sandbox for security testers. DVL intentionally includes outdated and exploitable software, providing its users with the necessary tools to practice security intrusion.[1]
OS Inheritance
Damn Vulnerable Linux is based on Slax[1], a popular bootable CD Linux distribution with a modular design. Slax provides a vast compact collection of pre-installed software and a well-designed user interface.[5]
Initial versions of DVL closely resembled Damn Small Linux, as the developers used the established techniques of DSL to provide small-sized (150MB) ISO releases.[4] The operating system also made use of the Linux 2.4 kernel in use by Damn Small Linux, as it provided additional security exploits that were fixed in later kernels.[4]
Development
Damn Vulnerable Linux was conceived and primarily developed by Dr. Thorsten Schneider, who integrated it into his university lectures on software security at Bielefeld University, Germany.[1] [3]
Schneider, then a member of the International Institute for Training, Assessment, and Certification (IITAC)[2], partnered with colleague Kryshaam of the French Reverse Engineering Team with the goal of creating a “plug-and-play system” that had “all the required tools installed” for training purposes, simply necessitating that the user to “run DVL in a virtual machine” to begin active learning.[4]
While initial releases maintained a close relationship to Damn Small Linux, the developers later decided to model the operating system after Backtrack 2.0. The latest release, Damn Vulnerable Linux 1.5: Infectious Disease, is downloadable as a 1.8GB ISO file.[6]
Target Audience
Damn Vulnerable Linux began as a functional tool for teaching students the importance of security. With its public release, Dr. Schneider and Kryshaam decided to continue this functionality, packaging a large collection of “tools, workbooks, text tutorials, and exploits” along with the operating system.[4] They later released their own mini-lectures on the main website, in the form of video tutorials. The first of these detailed how to cause a buffer overflow error.[4]
As with many Linux distributions, once in public domain DVL quickly found itself as the centerpiece of various community discussion groups. Users found alternative uses for the operating system, including as a secondary tool for testing the security exploitation and intrusion devices of Backtrack.[7]
Obtaining A Copy
The main website for Damn Vulnerable Linux has been offline for several months, reportedly having been taken offline due to German security laws.[9] It is possible to obtain an ISO copy of Damn Vulnerable Linux from Sourceforge.[6]
Installation / Startup
To install Damn Vulnerable Linux, make sure to obtan the most recent ISO file from Sourceforge.[6]
VMware Player Settings
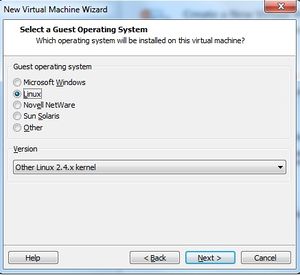
- Using VMware Player, Create a new virtual machine.
- Choose the option to install from disc image file, and browse to find the ISO location on your machine.
- When VMware prompts for the guest operating system, select ‘Linux’ and then ‘Other Linux 2.4.x kernel’ before proceeding.
- When naming the virtual machine, enter ‘DVL’ and select next.
- The default disk capacity and hardware settings are sufficient, so proceed through these stages without making any changes. Click Finish.
- Click enter to boot the system.
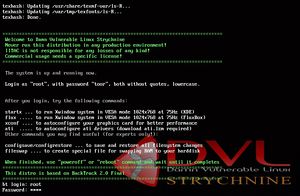
- After the system successfully boots, login as ‘root’ with password ‘toor’.
- To switch from the command line to a graphical interface, type ‘startx’.

Basic Operation
Usage Evaluation
References
[1] http://distrowatch.com/table.php?distribution=dvl
[4]http://web.archive.org/web/20090206193556/http://linux.com/articles/60267
[5]http://distrowatch.com/table.php?distribution=slax
[6]http://sourceforge.jp/projects/sfnet_virtualhacking/downloads/os/dvl/DVL_1.5_Infectious_Disease.iso/
[7]http://forums.hak5.org/index.php?showtopic=11389
[8]http://www.damnvulnerablelinux.com [9]http://www.reddit.com/r/linux/comments/fid3k/damn_vulnerable_linux_is_gone/
notes: dont have a box to properly install dsl on and attempt to break in with bt3