Difference between revisions of "COMP 3000 2011 Report: QuebeOS beta 2"
Jump to navigation
Jump to search
| Line 3: | Line 3: | ||
===Background=== | ===Background=== | ||
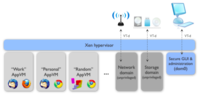
[[File:droppedImage.png|200px|thumb|left|A visual representation of the security system used by Quebes]] | [[File:droppedImage.png|200px|thumb|left|A visual representation of the security system used by Quebes]] | ||
Quebes is a very new Operating System based off the Linux OS combined with the Xen Hypervisor. This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. | Quebes is a very new Operating System based off the Linux OS combined with the Xen Hypervisor. This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. | ||
===Installation/Startup=== | ===Installation/Startup=== | ||
Revision as of 18:45, 16 October 2011
Part 1
Background
Quebes is a very new Operating System based off the Linux OS combined with the Xen Hypervisor. This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system.