COMP 3000 2011 Report: LPS
Background
This Distribution Report will be providing an analysis of the Lightweight Portable Security (LPS) operating system, which is developed and supplied by the Software Protection Initiative section of the United States Department of Defense (DoD).
LPS has been developed as an operating system to be used by government and military workers as a secure digital environment on systems that may not necessarily be secure. It has also been developed with a single use mentality. This means, there is no storage, and if the session becomes compromised due to malicious software, a simple reboot will produce a clean slate for the worker to use (Software Protection Initiative, 2011).
As of June 15th, 2011, LPS was approved by the Air Force Network Integration Center to access the Global Information Grid (GIG) for general telecommuting use (Software Protection Initiative, 2011). The GIG is described as a DoD system that includes any equipment, software, or service that transmits, stores, or processes DoD information, and provides any other associated services necessary to achieve information superiority (NSA, 2011).
The operating system has two variants, which can be obtained from the following locations:
Public ISO (137.3 MB Image) http://www.spi.dod.mil/docs/LPS-1.2.5_public.iso
Public Deluxe ISO (317.3 MB Image) http://www.spi.dod.mil/docs/LPS-1.2.5_public_deluxe.iso
Note: This report will be looking specifically at the Deluxe version of the distribution, which also provides Adobe Reader and Open Office.
The heritage of this operating system is not clearly documented anywhere, but based on the settings required for the Virtual Machine environment, it can be concluded that it is using a 2.6.x Linux kernel variant.
Installation and Startup
System Requirements
- A computer system with an x86 processor
- 512 MB of RAM (LPS-Public), 1 GB RAM (LPS-Public Deluxe)
- Wired, Wifi, or broadband cellular Ethernet (DHCP highly recommended)
- Ability to boot from either USB or CD-ROM (LPS is available on either media)
- CCID-compliant USB smart card reader (SCR 331 w/current firmware [>5.22])
Although LPS is meant to be used as a live boot distribution, for the purposes of this report and testing, VMPlayer 4.0 was used as the operating environment.
Installation was simple and straightforward. When setting up the VMWare Virtual Machine, VMWare Player was unable to detect the operating system automatically, so the Linux option “Other Linux 2.6.x kernel 64-bit version” was chosen.
Default settings were kept for the rest of the configuration, with the exception of customizing the virtual machine hardware memory. This value was changed from the default 384 MB, to 1024 MB, as per meeting the distribution system requirements.
Booting of the distribution took roughly one minute from start to the license agreement screen. Upon accepting the agreement, the desktop loaded almost instantly.
Basic Operation
With my configuration, there was 678.5 MB of free space left to be used.
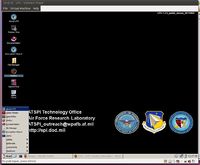
Upon viewing the distribution's desktop, the first thing that is noticeable is the striking similarity in appearance to a Windows operating system. There is a start menu, but instead of a Windows logo, the user will find Tux there. There are also Windows Show Desktop and Command Prompt icons. Show Desktop performs as expected, but the Command Prompt icon launches Xterm.
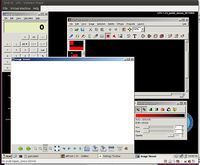
It is likely that most users of this operating system would be coming from a Microsoft background, so it does make sense that the developers would choose to make an experience that follows what one would expect in a Windows environment. The developers have went so far as to even apply skins onto various utilities to have them more closely represent the Windows equivalents. This can be seen in the screenshot below.
Going to Work
Since the operating system was meant to provide workers with a secure environment for telecommuting, an attempt was made to replicate a “workday”.
First, Open Office was used to create and save an assortment of text documents, and spreadsheets. Next, the FireFox browser was used to view a number of websites, including YouTube, WebCT, and CNN.com. All websites performed smoothly and as expected.
I was a little skeptical of logging into any websites, including my personal email, and banking. Now, this is not because I did not expect my session to be secure, but at a stage of preliminary analysis, I am a bit too paranoid to enter login credentials into a DoD operating system.
There are a number of remote connection options available, including Citrix Receiver, Remote Desktop, and a remote SSH client. The operating system should also allow for the use of a smart card reader that can contain the log in information required to remotely access a system. I was unable to test this features, since I lack a smart card reader, but I was able to use the SSH client to remotely connect to a computer.
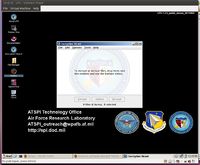
One of the features unique to this distribution that was tested was the Encryption Wizard. This is an encryption and decryption program that uses a 128-bit implementation of the Advanced Encryption Standard (AES) with a drag-and-drop interface (ATSPI Technology Office, 2011). It creates the ability to encrypt files using a pass key, with a PKI Certificate, or both, as well as add Meta Data, although this is not encrypted. Decrypting a file that was encrypted using the Encryption Wizard follows a similar point and click method. Both encrypting, and decrypting files was tested on the text documents created earlier in the session, and no problems were encountered.
After creating a number of files were created and downloading an assortment of PDFs, as well as extensive Internet browsing, an operating system restart was done to see if there would be any traces of the session. Upon completing the reboot, all files from the previous use of LPS were gone, and web history from FireFox had also been cleared.
Usage Evaluation
Upon using LPS, it does appear to provide all of the features that would typically be required in an average work session. Documents can be viewed, and edited, and websites are accessible. I also assume that the remote access utilities available that were not tested, work as well.
However, there are a number of concerns I have with regards to how secure the operating system actually is, because of some of the available options that an attacker could use to takeover the session, largely browser based.
LPS uses the latest versions of much of its software, including Adobe Reader and Open Office, but Firefox is using version 3.6.2.2, when the latest version as of this writing 7.0.1, and Adobe Flash 10.3.183.10, when the latest version as of this writing is 11. Using out of date versions of software is typically something that raises a bit of concern.
Next, the browser itself does not use any common extensions that would be expected in a secure environment, such as NoScript, which helps the user to block unwanted scripts, extensions, and other malicious things from running in their browser (NoScript, 2011). There actually do not appear to be any restrictions on what extensions a user can install, or disable, including built in DoD extensions.
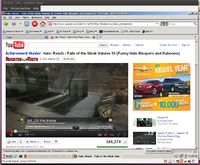
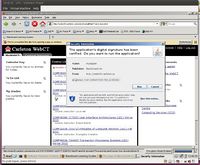
Not only can a user install potentially vulnerable extensions, but as can be seen from the following screenshot, “signed” Java applications can be executed as well. In the case of WebCT, this not an issue, but it does provide the opportunity for a malicious attacker to use the Java Applet Attack Vector provided in tools such as the Social Engineering Toolkit (Social Engineer, 2011).
The lack of basic checks in place when it comes to browser security seem counterintuitive for a “secure” operating system. Even with the ability to create a clean session with a system reboot, it is hard to know how much information an attacker could gain before such a reboot occurs.
References
ATSPI Technology Office. Lightweight Portable Security (LPS) Public Edition (LPS-Public) User’s Guide. Web. 10 Oct. 2011. <http://spi.dod.mil/docs/lpsmanual.pdf>.
"Global Information Grid – NSA/CSS." Welcome to the National Security Agency - NSA/CSS. NSA. Web. 10 Oct. 2011. <http://www.nsa.gov/ia/programs/global_industry_grid/index.shtml>.
NoScript - JavaScript/Java/Flash Blocker for a Safer Firefox Experience! - What Is It?. NoScript. Web. 10 Oct. 2011. <http://noscript.net/>.
"The Official Social Engineering Framework - Computer Based Social Engineering Tools: Social Engineer Toolkit (SET)." Social Engineering - Security Through Education. Social Engineer. Web. 10 Oct. 2011. <http://www.socialengineer.org/framework/Computer_Based_Social_Engineering_Tools:_Social_Engineer_Toolkit_(SET)>.
"Software Protection Initiative - Lightweight Portable Security." Software Protection Initiative. Software Protection Initiative. Web. 10 Oct. 2011. <http://www.spi.dod.mil/lipose.htm>.