COMP 3000 2011 Report: Privatix
Part 1
Background
The name of our chosen distribution is the Privatix Live-System. The target audience for this system are people that are concerned about privacy, anonymity and security when web-surfing, transporting/editing sensitive data, sending email etc. Therefore, the goals of this distribution are mainly security and privacy related which means being able to provide security-conscious tools and applications integrated into a portable Operating System (OS) for anyone to use at any time. The distribution is meant to be portable, coming in the form of a live Compact Diak (CD) which can be installed on an external device or a Universal Serial Bus (USB) flash drive with an encrypted password to ensure that all your data remains private, even if your external device is lost or compromised. It should be noted that the live CD is only meant for installing the OS onto a USB in order to provide a portable, privacy conscious OS. The user should not solely rely on the live CD as the OS does not yet implement password protection. This is due to the fact that there are no user accounts on the live CD, user accounts are only implemented once the full OS is installed on a USB. The Privatix Live-System incorporates many security-conscious tools for safe editing, carrying sensitive data, encrypted communication and anonymous web surfing such as built in software to encrypt external devices, IceWeasel and TOR. <ref name="privatix home">Privatix home page(Last accessed 10-10-11)</ref>
This Privatix Live-System was developed in Germany by Markus Mandalka. It may be obtained by going to Markus Mandalka's website and navigating to the download page (Mandalka), selecting the version you wish to download (we chose the English version) and downloading it. The approximate size of the Privatix Live-System is 838 Megabytes (MB) for the full English version (there are smaller versions available which have had features such as GNOME removed).<ref name="Privatix download page">Privatix download page(Last accessed 10-10-11)</ref>. The Privatix Live-System was based off of Debian (Debian).
Installation/Startup
Currently we have Privatix installed on an 8 Gigabyte (GB) USB stick in order to utilize the full power of the OS. However, Privatix can be used in a few ways other than installing it on an external device such as on a live CD/Digital Video Disk (DVD), or in a virtualized environment such as VirtualBox. It should be noted, however, that the full potential of the OS is only unlocked once the OS has been installed on an external device as it was meant to be. One main flaw in using either a virtual environment or the live CD is that user accounts, and hence password protection, are not implemented until the OS has been installed on an external device.
To install the Privatix-Live System, the user must first download the .iso from the download page (Mandalka). Once the .iso file is downloaded, it is possible to either burn the operating system to a CD/DVD, use VirtualBox, or install it to a USB stick.
CD/DVD
To install and boot Privatix with a CD/DVD, simply burn the operating system to a disk and boot from the CD/DVD created when prompted to in the BIOS. While using the Live CD, the user will have access to almost all features of the operating system. However, because no profiles were setup, if the user locks the computer, there will be no way to unlock it as no password was not setup. Note that the main purpose of the live CD/DVD is to install the OS on an external device.
VirtualBox
Using VirtualBox requires simply having VirtualBox installed, and when prompted for the installation media to select the .iso file downloaded for Privatix.
When the system starts up select the Live option. This brings up the main Desktop, while using VirtualBox the user will have access to all features available when using Privatix with the Live CD. However there is one small extra level of security, this is provided by the host operating system. this extra layer of security takes the form of the profile system of the host operating system.
USB
To install Privatix onto a USB stick, you first must be booted into Privatix Live through a CD/DVD. Then you need to click the install icon on the Desktop to begin installing to a device. It is then possible to select a device for Privatix to install itself on. The installer will ask you if you would like to fill your device with blank data, this makes accessing data/recovering what was originally on the device much harder. The installer will prompt you for a user password, as well as an admin password. The installer will then start it's time consuming process of installing Privatix to the device.
To boot into Privatix from the device, you can stop the computer booting, and then boot into the external device. During booting, Privatix will prompt you for your the password set up during the installation.
Basic Operation
On An External Device
The main way of utilizing the Privatix Live-System is done by installing the system on an external device. In our case, we used an 8 GB USB stick. When the system is installed on an external device, it is easy to use the system for its intended purpose--having portable anonymous and secure system. We tested this portable version of the system on several laptops with no trouble and no noticeable discretion in use between the different machines. We attempted to use the the system for the following use cases: anonymous web browsing, secure email, data encryption and secure data transportation.
Apart from this, Privatix also came with OpenOffice applications for editing all types of data and much of the basic GNOME functionality, including (but not limited to):
- Pidgin IM and Empathy IM Client for instant messaging
- Evolution Mail for sending and retrieving email
- gedit for text editing
Anonymous Web Browsing
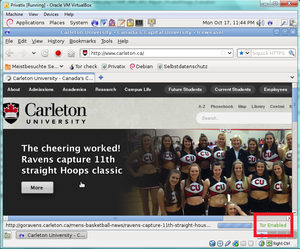
The main thing we liked about this system was the secure and anonymous web browsing. The default browser in the system is IceWeasal (an older version of GNU IceCat--a re-branding of FireFox compatible with both Linux and Mac systems) which comes equipped with security features not available by default in FireFox. The main add on that I liked was that The Onion Router (TOR) is installed and enabled by default (it can be disabled if the user wishes). TOR is an open source project meant to provide absolute anonymity online--mainly preventing anyone from learning your location or browsing habits--by routing webpage requests through virtual tunnels made up of individual TOR nodes. Since no two "paths" for a request are ever the same there is no way for your traffic to be monitored. <ref name="TOR Project - About">TOR Project - About(Last accessed 10-10-11)</ref>
Secure Email
The Privatix Live-System also came equipped with the security-conscious email client IceDove--an unbranded ThunderBird mail client (a cross-platform email client that provides government-grade security features). The email client was easily setup and used, supporting digital signing and message encryption via certificates by default (as with TOR, this could be disabled if the user wished). <ref name="icedove">IceDove(Last accessed 10-10-11)</ref>
Data Encryption
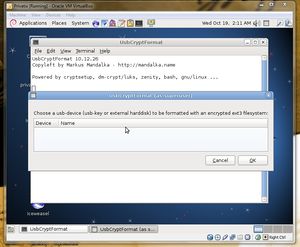
The Privatix Live-System also has the ability to encrypt external devices (besides the external device that the system is installed on). This meant that we could have an unlimited amount of encrypted data, not being limited to the size of the external device that the system itself is installed on. The ability to encrypt secondary external devices is very handy as much of the space on the external device that Privatix is installed on is taken up by the system itself, especially if one fills the device with blank decoy data on installation. The encryption software was easily used, well designed and was able to be utilized by absolute beginners of the system.
Secure Data Transportation
There are two ways that Privatix fulfills its secure data transportation goal:
- When saving data on the external device with the Privatix Live-System, the data is automatically encrypted and is also password protected (since the portable version of Privatix requires a password to use it). <ref name="Privatix FAQ">Privatix FAQ(Last accessed 10-10-11)</ref>
- As mentioned above, Privatix allows for the encryption of secondary external devices, hence meaning that data can be securely transported without even having the Privatix Live-System with you.
General Use
Even with the additional security features not available in other distributions, Privatix would still be a very desirable live system to use. It is portable, especially once installed on an external device, and easily used with little bloatware. The default applications such as OpenOffice for data editing, Pidgin for instant messaging, various graphics editors, video player, and CD burner/extractor ensured that they system was still perfectly functional for everyday use, even with security, not intense functionality, being the main focus.
Live CD and Virtual Box
We found that running Privatix using the live CD and VirtualBox was equivalent.
When booting the live CD in VirtualBox, there are certain key features of the Privatix Live-System you are missing (mainly because these features are meant for the portable version to be installed on an external device). However, just booting from the live CD still gives a lot of the functionality I would use the system for--mainly the anonymous web browsing, secure email and data encryption. The key differences were the lack of portability and the inability to save any data on the live CD or VirtualBox environment.
When using only the live CD or VirtualBox all files are deleted when the system is shut down. In addition to, any files saved to the desktop by the user will not appear. They will be hidden from view, but can be viewed by opening the terminal and navigating to the desktop and running the ls command.
The main flaw in only using the system in these mediums is that the added protection of having a user account and password to access the system are no present on the live CD or when using Privatix in a virtual machine. This is due to the fact that Privatix does not implement user accounts and password protection until it has been fully installed onto an external device. As the main goal of this distribution is privacy, it would be highly recommended that the user fully install the OS onto an external device for the added security of password protection.
Usage Evaluation
During our use of Privatix, we found it preformed on par for what it was described as, a secure and portable system. The tools provided to encrypt data and the secure browser with add-ons for anonymity especially supported this belief. However we also found some parts of the distribution that were a cause for concern. To begin with, there was a slight language barrier as the system was originally written in German. This was made apparent by the frequent grammar mistakes in both the existing English documentation and the operating system itself indicating that English was not the primary language for the writers of this operating system. Most of the documentation for the operating system is also in German. Those who maintain Privatix and its project website are in the process of translating all their documentation as to be available in both English and German, though currently most of the supporting documentation and FAQ are in German. This made it hard to troubleshoot anything that went wrong with the system during installation or use.
We also noticed that there was no wireless drivers on either portable versions of the OS (installed on an external device or simply using the Live CD or booting up in a virtual machine) so wireless networks could not be connected to. This causes a problem because an operating system on a USB stick should be completely portable, however this driver requires you to have a hard line to use the Internet. It was also noticed that when using Privatix in VirtualBox that even though there was no wireless drivers in Privatix, the wireless capability was provided by the host OS (Windows).
Lastly, when we tried to install Privatix onto a USB it took several attempts. We discovered that to avoid many of the problems we encountered, it is better to use a larger (preferably at least 8GBs) external device for installation and to defer from filling the external device with blank decoy data during installation on an external device.
However once connected to the Internet, all software seems to work as it should. The more basic applications such as OpenOffice, the instant messaging and email clients, multimedia applications etc. function with no problems encountered, working much as they do in any other Linux distribution. The security tools also seem to work as they should. However since we do not know how to test the limits of its security measures we do not know for sure how secure these programs actually are. Overall, Privatix seems to be a very functional and portable distribution, allowing users access to standard applications for tasks such as editing and transporting data, sending/receiving email, instant messaging and multimedia applications with the added bonus of being completely secure and anonymous.
Part 2
Software Packaging
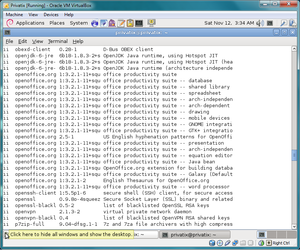
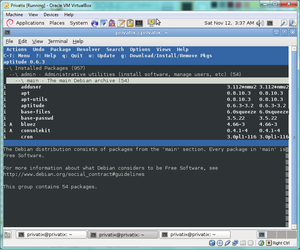
The packaging format that was used for the Privatix-Live System was DEB (based on the Debian packaging format). <ref name="privatix distrowatch">Privatix Distrowatch Page(Last accessed 12-18-11)</ref> The utilities used with this packaging format were dpkg and aptitude. Dpkg is used as the operating system's package management utility, with aptitude acting as the more user-friendly front end version. Aptitude made finding a list of installed packages quite easy. Aptitude allows you to see a full list of installed packages, with the packages being segregated into categories such as mail, web, shells and utils. As well as using aptitude, the command line can be used to access a list of installed packages. To do this, input the following in terminal and a list of all installed packages is generated. <ref name="dpkg man page">Dpkg Man Page(Last accessed 12-11-11)</ref>
$ dpkg -l
Though knowing how to do this in command line is useful, we found that using aptitude was generally better as the packages are segregated into categories which made viewing the list of installed packages more simple.
To add a package within Privatix, we found the easiest way was to use the one of the following commands provided by dpkg:
$ dpkg -i <package name>
or
$ dpkg --install <package name>
These commands function in the same way which means they will either install a package, or upgrade already installed versions of the package. <ref name="dpkg man page">Dpkg Man Page(Last accessed 12-11-11)</ref>
To remove a package within Privatix, we found the easist way was to use either of the following commands provided by dpkg:
$ dpkg -r <package name>
or
$ dpkg -P <package name>
When using "dpkg -r <package name>", everything related to the package except the configuration files are removed. To fully remove a package, however, we used "dpkg -P <package name>" which removes the entire package, including the configuration files. <ref name="dpkg man page">Dpkg Man Page(Last accessed 12-11-11)</ref>
We found that the software catalog for this distribution was quite extensive, especially since this distribution is meant to be portable. Privatix includes all the standard packages included with Debian (e.g. libc), as well as several other utilities meant to increase security and privacy while using the system such as IceDove, TOR and TORButton.
Major Package Versions
For this section of the report, we needed to speculate as to why a certain version of a package was included, not just the package itself. We determined, with the release date of Privatix <ref name="privatix distrowatch">Privatix on Distrowatch(Last accessed 12-19-11)</ref>, that the usual reasoning behind a certain version of a package being included was that the included version was the stable release of the package at that time. We also needed to determine how heavily modified by the distribution's author packages included within our distribution were. However, the distribution's author has stated that everything included is mainly based on Debian. <ref name="privatix documentation">Privatix Documentation (German)(Last accessed 12-11-11)</ref> The packages within Privatix have not been modified, the distribution's author has mainly brought together several security and privacy conscious utilities into one distribution for portable and daily use. As such, many of the packages that come with the standard install of Privatix have been included since they are included with the standard install of Debian at the time this distribution was made. Please also note that this reference was taken from the main page of the distribution but that, to view it, you will need to translate it (we used Google translate) as much of the documentation for this distribution is in German.
|
Category |
Package |
Version |
Upstream Source |
Vintage |
Package Details |
|---|---|---|---|---|---|
| Kernel | linux-base | 2.6.32-31 | None Provided | This version of the kernel was released in December of 2009, making it just under two years old. <ref name="linux kernel">Linux Kernel v2.6.32 Info Page(Last accessed 12-11-11)</ref> The newest stable version of the Linux kernel was released just yesterday (11/11/2011), this version being listed as 3.1.1. <ref name="current kernel">Current Stable Linux Kernel(Last accessed 12-11-11)</ref> This puts the version of the Linux kernel on Privatix as being two years behind the current stable version of the Linux kernel. | We believe that these packages were included as it is one of the standard packages for the Linux kernel included in the standard install of Debian and was the current stable release of this package at the time Privatix was released. |
| linux-image-2.6.32-5-686 | 2.6.32-31 | ||||
| linux-image-2.6-282 | 2.6.32+39 | ||||
| libc | libc-bin | 2.11.2-10 | http://www.eglibc.org | This version of libc was released in January 2011, making it approximately 11 months old.<ref name="eglibc">eglibc Source Package on Debian(Last accessed 12-11-11)</ref> This version is also the current stable version of libc, as listed on Debian. <ref name="eglibc">eglibc Source Package on Debian(Last accessed 12-11-11)</ref> However, a newer, unstable version (version 2.13-21), is currently undergoing testing. | This package was included as it is one of the standard packages for Debian and was the current stable release of this package at the time Privatix was released. |
| libc6 | |||||
| Shell | bash | 4.1-3 | http://tiswww.case.edu/php/chet/bash/bashtop.html | This version of bash was released in, approximately, April 2010. <ref name="bash">bash Source Package on Debian(Last accessed 12-11-11)</ref> It is also the current stable version of bash. <ref name="bash">bash Source Package on Debian(Last accessed 12-11-11)</ref> However, last month, version 4.2 of bash was pushed into testing and became the current experimental version.<ref name="bash">bash Source Package on Debian(Last accessed 12-11-11)</ref> | This package was included as it is one of the standard packages for Debian and was the current stable release of this package at the time Privatix was released. |
| Utilities | busybox | 1:1.17.1-8 | http://www.qtsoftware.com/ | This version of busybox was released in, approximately, November 2010. <ref name="busybox">busybox Source Package on Debian(Last accessed 12-11-11)</ref> It is also the current stable version of busybox as listed on Debian. <ref name="busybox">busybox Source Package on Debian(Last accessed 12-11-11)</ref> | This package was included as it is one of the standard packages for Debian and was the current stable release of this package at the time Privatix was released. |
| Software Packaging | dpkg | 1.15.8.10 | http://wiki.debian.org/Teams/Dpkg | This version of dpkg was released in February of 2011, making it 10 months old. <ref name="dpkg changelog">Dpkg Changelog(Last accessed 12-11-11)</ref> The current stable version of dpkg, as listed on Debian, is version 1.15.8.11 which was released in April of 2011. <ref name="dpkg">Dpkg Source Package on Debian(Last accessed 12-11-11)</ref> This would put the version of dpkg included with Privatix at 3 months behind the latest stable version. | This package was included as it is one of the standard packages for Debian and was the current stable release of this package at the time Privatix was released. |
| Web Browser | IceWeasel | 3.5.16-6 | None Provided | This version of IceWeasel was released in March 2011, making it 9 months old. <ref name="iceweasel">IceWeasel Source Package on Debian(Last accessed 12-11-11)</ref> The newest stable version is version 3.5.16-11 which was released in November 2011. <ref name="iceweasel">IceWeasel Source Package on Debian(Last accessed 12-11-11)</ref> This would put the version of IceWeasel included with Privatix at 9 months behind the latest stable release. | IceWeasel was included within this distribution as it is a more security conscious browser than more mainstream browsers such as Mozilla Firefox. IceWeasel, an older version of GNU IceCat (a rebranding of FireFox), comes equipped with security features not available by default in FireFox. |
| Tor | 0.201029-1 | https://www.torproject.org | This version of TOR was released in January 2011, making it 11 months old. <ref name="tor changelog">TOR Changelog(Last accessed 12-11-11)</ref> The latest stable release of TOR is version 0.2.1.30-1 which was released in July 2011. <ref name="tor">TOR on LaunchPad(Last accessed 12-11-11)</ref> | This package was included to help increase security, anonymity and privacy while web browsing which is one of the main goals of the Privatix distribution. For more information on TOR, see the Basic Operation section of the report, under Anonymous Web Browsing. | |
| TOR Button (xul-ext-torbutton) | 1.2.5-3 | https://www.torproject.org/torbutton/ | This version of TOR Button was released in October 2010, making it just over a year old.<ref name="torbutton">TORButton(Last accessed 12-11-11)</ref> The newest stable version of this program is version 1.4.4.1 which was released last month. <ref name="torbutton">TORButton(Last accessed 12-11-11)</ref> This would put the version of TORButton included with Privatix at about a year behind the latest stable release. | This package was included in order to add to the functionality of TOR. This add-on allows the user to enable and disable TOR with the push of a button, located in the corner of their browser. | |
| icedove | 3.0.11-1+s | None Provided | This version of IceDove is the current stable version as listed on Debian. <ref name="icedove debian">IceDove Source Package on Debian(Last accessed 12-11-11)</ref> However, this version was included within Privatix before it was made stable. It was released as an unstable version in December 2010 and was later released as the current stable version in October 2011. <ref name="icedove debian">IceDove Source Package on Debian(Last accessed 12-11-11)</ref> | This email client was included due to the fact that it is a more security-conscious email client, providing government-grade security features, than others such as the regular version of ThunderBird. For more information on this program, refer to the Basic Operation section of this report under Secure Email. | |
| Other | pidgin | 2.7.3.1+sq | http://www.pidgin.im | This version of the Pidgin was released in October 2010, and is also the current stable version of Pidgin as listed on Debian. <ref name="pidgin">Pidgin Source Package on Debian(Last accessed 12-11-11)</ref> | This package was included as it is one of the standard packages for Debian and was the current stable release of this package at the time Privatix was released. |
Initialization
Privatix generally follows the same initialization process as Debian. Privatix initializes by first executing first the BIOS then the boot loader code. <ref name="debian boot process">Debian Boot Process(Last accessed 12-11-11)</ref> Privatix uses the same boot loader as Debian which is System V initialization. /etc/inittab is the configuration file, with the /sbin/init program initializing the system following the description in this configuration file. <ref name="debian boot process">Debian Boot Process(Last accessed 12-11-11)</ref> inittab will set the default run level of Privatix, which is run level 2. Following this, all the scripts located in /etc/rc2.d are executed alphabetically. <ref name="debian boot process">Debian Boot Process(Last accessed 12-11-11)</ref> These scripts are:
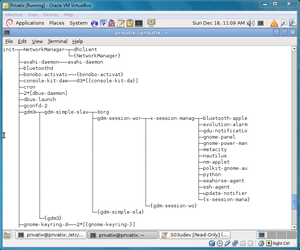
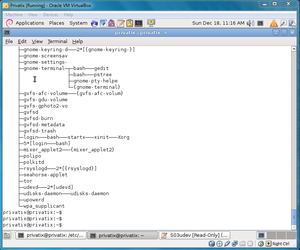
- S01polipo: polipo web cache--a small and fast caching web proxy
- S01rsyslog: enhanced multi-thread syslogd which is Linux system logging utility
- S01sudo: provides sudo
- S02cron: starts the scheduler of the system
- S02dbus: utility to send messages between processes and applications
- S02rsync: opens rsync--a program that allows files to be copied to and from remote machines
- S02tor: starts TOR (for more information, see above)
- S03avahi-daemon: starts the zeroconf daemon which is used for configuring the network automatically
- S03bluetooth: launches bluetooth
- S03networ-manager: starts a daemon that automatically switches network connections to the best available connection
- S04openvpn: starts openvpn service--a generic vpn service
- S05gdm3: script for the GNOME display manager
- S06bootlogs: the log file handling to be done during bootup--mainly things that don't need to be done particularly early in the boot process
- S07rc.local: runs the /etc/rc.local file if it exists--by default this script does nothing, it is used only to exit
- S07rmologin: removes the /etc/nologin file as the last step in the boot process
- S07stop-bootlogd: runs the /etc/rc.local file again, if it exists--by default this script does nothing, it is used only to exit
Following this, the system is initialized. The processes running on the newly initialized system and what initializes them are as follows:
| Process Name | Description | Initialized By |
|---|---|---|
| NetworkManager | Daemon that automatically switches network connections to the best available connection | S03networ-manager init script |
| avahi-daemon | zeroconf daemon which is used for configuring the network automatically | S03avahi-daemon init script |
| bluetoothd | Enables bluetooth to be used | S03bluetooth init script |
| cron | Scheduler of Debian systems | S02cron init script |
| dbus-launch | Utility to send messages between processes and applications | S02dbus init script |
| gdm3 | GNOME display manager | S05gdm3 init script |
| gnome-screensav | ||
| gnome-settings- | ||
| gnome-terminal | ||
| polipo | polipo web cache--a small and fast caching web proxy | S01polipo init script |
| tor | TOR is an open source project meant to provide anonymity online--mainly preventing anyone from learning your location or browsing habits--by routing webpage requests through virtual tunnels made up of individual TOR nodes. Since no two "paths" for a request are ever the same there is no way for your traffic to be monitored. | S02tor init script |
We found this information by first confirming that Privatix used the same style of initializing as Debian. Once we ascertained this, we researched the Debian boot process. Privatix followed the same steps up until the loading of the scripts, which had some scripts that differed from Debian (e.g. TOR). Following this, we researched each of the scripts run on Privatix's default boot level of 2. The scripts are listed above, in the order they execute. To find the purpose of each of the scripts and what programs they opened, we manually went through each of the scripts. To find the processes running on the newly initialized system, we used the command "ps tree". Once we had a list of the running processes, we researched the purpose of each process. To find how each process was initialized, we manually searched through the initialization scripts and matched each process with their initialization script.
References
<references />