Report: TAILS
PART 1
Background
The distribution is known as The Amnesic Incognito Live System (TAILS). The goal of the distribution is to provide anonymity for the user and thus targets any consumers that require a higher level of privacy when using the internet and do not want to leave traces of their activity on the host file system. TAILS is an extension of the Debian GNU/Linux distribution system.
To achieve online anonymity, TAILS uses the Tor Network. The Tor Network is an open network that is accessible through free software. Tor is designed to make it difficult for anyone to trace your internet traffic. It uses a network of virtual tunnels to protect the user from “traffic analysis” (eavesdropping, IP spoofing, ARP spoofing, etc...). To combat these attacks it sends your data packets as multi-hop circuit of relays. Each relay only knows the address of the relay that provided the data and the relay it will provide the data too. This effectively erases the track back to the sender. Any eavesdropper will only be able to trace the message back to the relay before. One drawback is that the Tor network does not encrypt data from relay to relay only from the sender to the first relay and from that relay back to the sender. This prevents the eavesdropper from being able to view your data at the first relay but does not prevent them from viewing your data at other relays. Although the onus is on the website the user is communicating to provide the end-to-end protection TAILS does provide this protection when using IRC or Email through software that comes with the system. Another drawback is that most if not all modern Web Browsers use JavaScript, Adobe Flash and Cookies, these have been proven to occasionally bypass the anonymity feature. To combat this TAILS provides its own Web Browser based of Firefox called Iceweasel. Unfortunately some sites will not work with it due to its limitations.
To help protect against leaving traces on the host computer TAILS runs as an independent operating system unless made to do otherwise. TAILS is a Livedistro that runs off a bootable USB or CD (USB is faster) requiring no installation on the host PC. The only memory TAILS accesses is RAM which is overwritten on PC shutdown (unless the shutdown is abrupt, such as in a power failure) leaving no trace on the system. If you choose to do so you can run TAILS through as a virtual machine but this negates the above protection feature as both the virtual machine and the host OS will leave traces on the host PC. The other drawback is that as you are not using the host PC file storage system you need to use a separate storage system such as another USB drive to save any data that you work on while in TAILS.
TAILS can be obtained for free from the internet. The latest version is 0.8.1 and it was released on October 16th, 2011. It downloads as an ISO image of 579 Mb in size. The home website for TAILS has an interesting feature where it allows the user to verify that the ISO they downloaded is authentic as the genuine version is encoded with a cryptographic signature. The user can either do this through a check through Firefox, using an add-on, or through software known as Gpg4win which is essentially an encryption and decryption software. This just shows the level of commitment the developers have to user privacy and security.
Installation/Startup
Once the user has downloaded the ISO image they will need to make the USB or CD key bootable from that ISO. I used the USB approach and used the Universal USB Installer software (version 1.8.6.8). Once the USB key has been created the user simply uses makes the host PC boot to the USB key upon restart. Upon restart the user is presented with a boot menu where they can select their language. One the distribution system loads the user is presented with a desktop UI and TAILS automatically launches an Iceweasel and tests the TOR connection.
The actual start-up of the distribution system from the USB key was very fast. The load time was approximately 30-45 seconds once the language at the boot menu is chosen. As TAILS is meant to run as a Livedistro system I did not use any virtualization software to get it running (although the option is there if you so choose) and as such do not have a screen shot of the actual loading process.
Basic Operation
The first impression is that TAILS is much like any Debian based distribution system. The desktop looks very similar as it contains the same status bar on the bottom of the screen and the menu bar up top, however compared to say the latest version of Ubuntu, TAILS does not come preloaded with many applications.
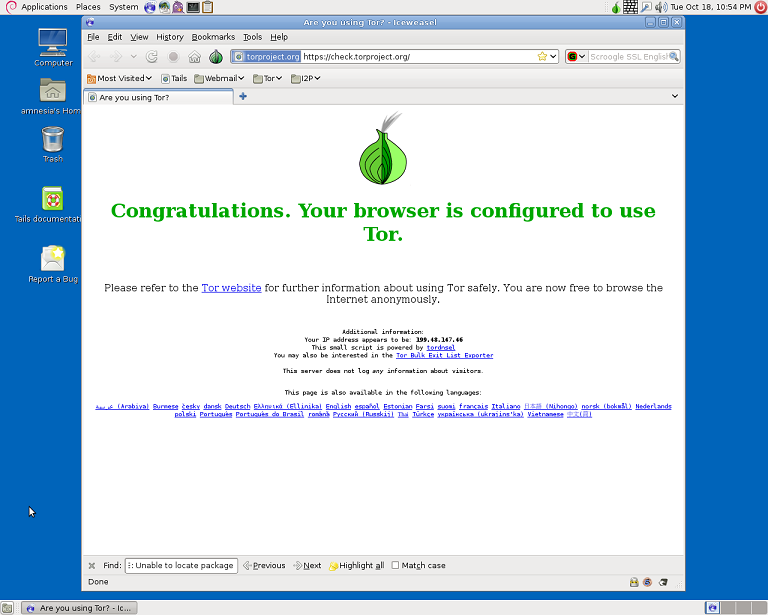
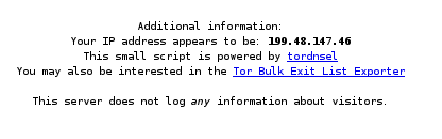
As TAILS first runs a web browser to TOR to test the network connection it provides you with the falsified IP address your system uses when on the network. Checking the TAILS distribution using ifconfig it showed that the IP addresses did not match up.
To essentially control how you use the TOR network TAILS provides software known as Vidalia (pictured as an onion in the top right hand corner of the UI). The application is automatically launched once the system connects to a network. To open the control panel double click the icon. Once the control panel is opened the user can do the following:
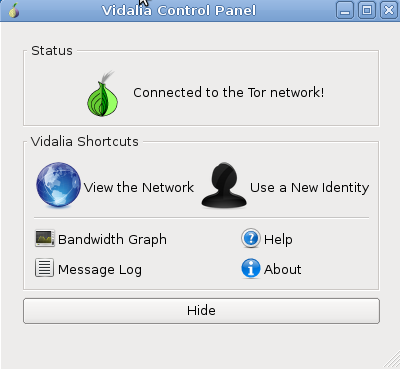
• View the Tor network: This shows a list of relays, currently used routes and their status
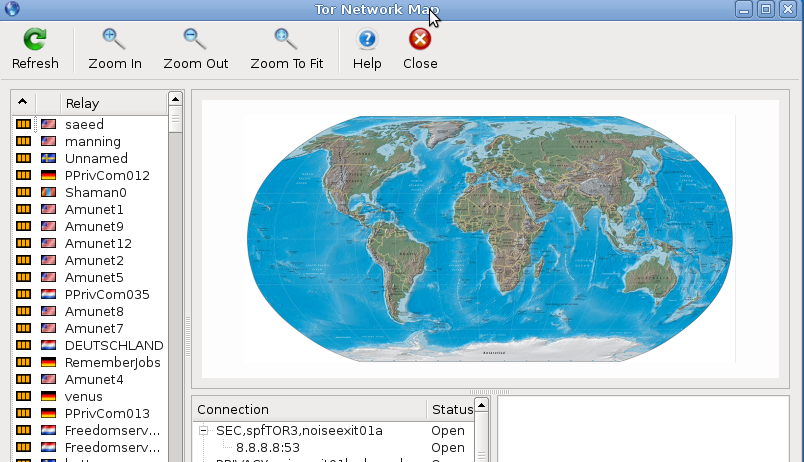
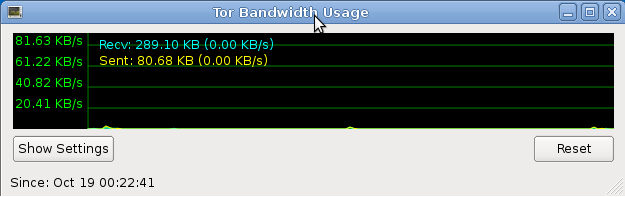
• Choose a new identity to use: Tears down all current circuits and creates new ones. Your route is modified into a new one. • View the bandwidth graph: This allows the user to check the current bandwidth usage on their circuit.
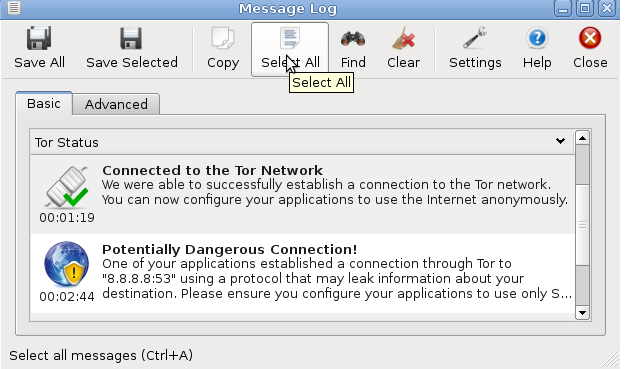
• Connect through a bridge: If your ISP prevents you from using the Tor network you can “bridge” into the Tor network using Vidalia by going to the settings, network and then selecting the “My ISP blocks connections to the Tor network” checkbox. This will bring you to a form to add a Tor bridge as an entry point. • Setting up a Tor relay: Vidalia gives the user the option of setting themselves up as a Tor relay to help the Tor network. • Message Log: Acts as an event viewer for the Tor network. Displays messages such as if the Tor software is running and if there is a dangerous connection
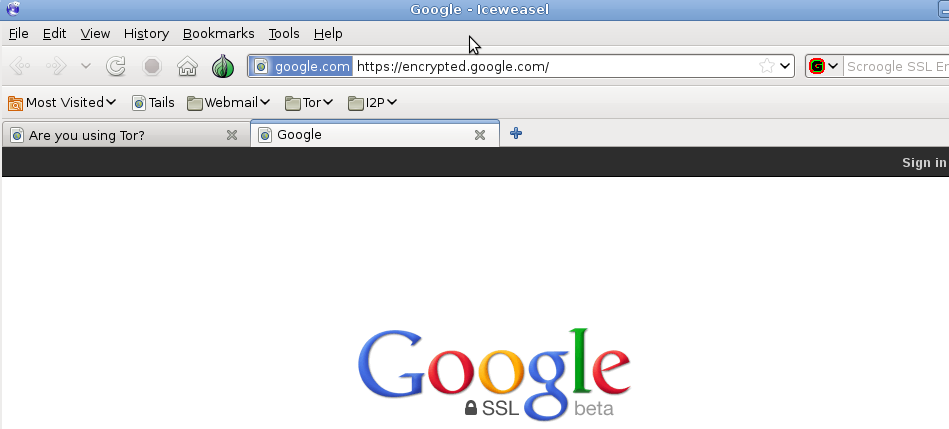
When using the web browser Iceweasel you will notice that all connections that can be encrypted are through SSL. The indication is in the address name of the website which starts with https:// instead of the usual http:// (the s standing for secure). I found that web browsing was slower than usual due to the relay of packets through the Tor network.
The only problem I ran into upon start-up was a functionality issue as even though TAILS runs of GNOME very little of the utilities were actually present including gnome-screenshot. It was necessary to install the utilities. Besides that the only other issue I experience with the initial setup and while trying some of TAILS’s features was the noticeable lag when trying to connect to websites.
Usage Evaluation
In the end I found TAILS to be quite similar to most Debian distributions I have used. The extra security features are interesting to explore. I do find that TAILS goes well beyond the other distributions I’ve played with when it comes to security as is evident by its focus on end-to-end encryption, use of the Tor network and refusal to leave traces on the host OS. The only issue is the lack in speed when using the Tor network to connect to websites but if the user is willing to forgo the entire purpose of TAILS they can download a normal Web Browser such as Firefox.
PART 2
Software Packaging
As TAILS is modeled off Debian GNU/Linux distribution it uses the Debian packaging format for its software packages. As with most other Debian distributions TAILS comes preloaded with some of the usual software packages such as OpenOffice.org, Iceweasel and GNOME-terminal. In total TAILS comes preloaded with 1096 packages as is shown by the Synaptic Package Manager on startup. TAILS uses the Advanced Packaging Tool (APT) system to manage the installation and removal of software. It is a front end user interface for the dpkg package utility run by Debian. Where dpkg is used on inidividual packages the apt tools in the apt package (such as apt-get) manage the relatioins between the packages. I primarily used the man page for dpkg to find the necessary information for this section.
To get a list of the packages that are installed the user can search the /var/log/dpkg.log file. This will provide the user with a list of when a certain software package was installed, removed or updated.
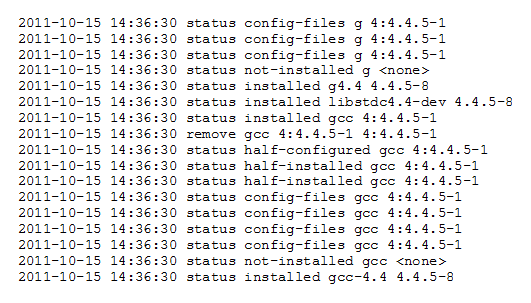
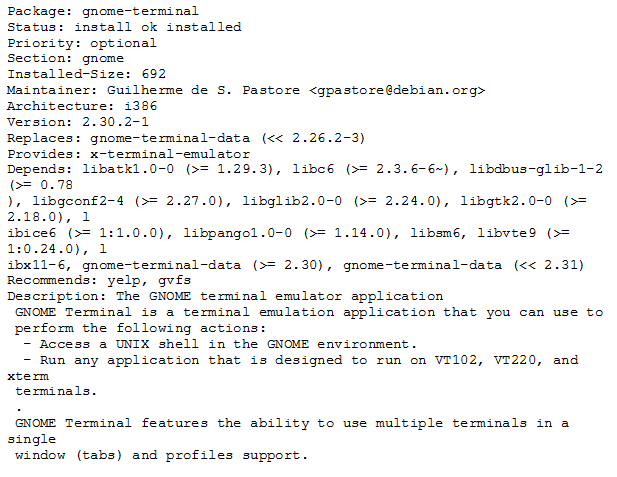
For more in depth information on the packages such as the install-size, version, dependencies and description the user can view the /var/lib/dpkg/status file.
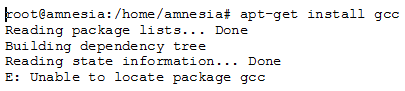
To add and remove packages the user would use the apt-get package mentioned earlier. To insatll a package the user would type the following command: apt-get install [package_name]. The user can specify more than one package at a time. To remove packages the user would type the following command at the command line prompt: apt-get remove [filename]. As with install the user can specify more than one filename.A set of options are available in conjunction with these commands such as, -d which specifies to only download the package. Unfortunately for TAILS this function does not seem to work. There is always an error: Unable to locate package [filename].
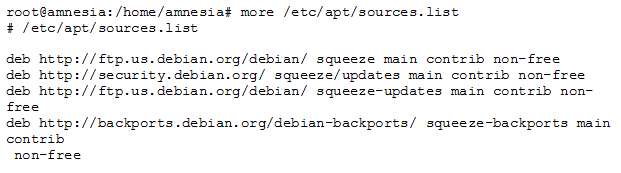
I checked the /etc/apt/sources.list file which contains the locations that apt checks to download the packages. the output is consistent with an Ubuntu distribution installation:
To install the packages I had to use the Synaptic Package Manager utility that comes available with TAILS. This is a front end graphical interface for apt that gives a visual representation of the command line commands such as apt-get install [filename]. To install a certain package you open the interface main window and search for the package name. Once located you select the package and double click. You will presented with a window requesting you mark the package for install.
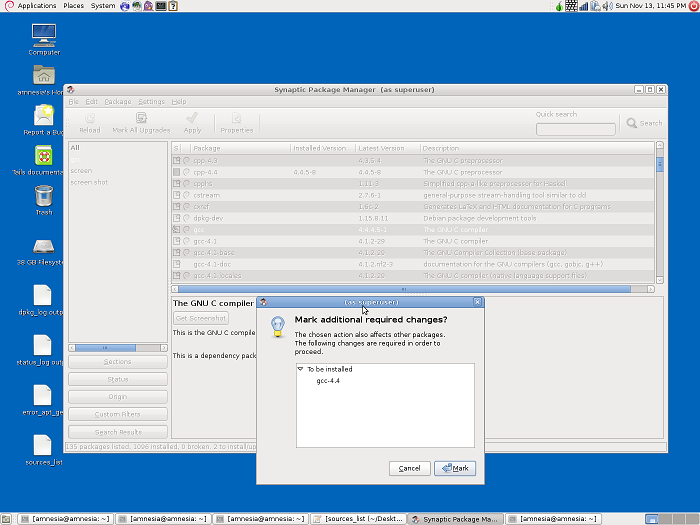
Once the package has been marked for install the user clicks the "Apply" button in the toolbar and the package is installed.
Major Package Versions
Initialization
References
http://tails.boum.org/index.en.html
https://www.torproject.org/about/overview.html.en
http://distrowatch.com/table.php?distribution=incognito
http://en.wikipedia.org/wiki/The_Amnesic_Incognito_Live_System
http://www.linuxjournal.com/content/tails-projects-amnesic-incognito-live-system-tails