COMP 3000 2011 Report: DEFT Linux
Part 1
Background
The Linux distribution we chose was DEFT – Digital Evidence and Forensic Toolkit – Linux. Built on xubuntu, DEFT is a live CD designed for police, investigators, system administrators and other linux and securities enthusiasts.
DEFT finds its origins in the Ubuntu/Debian linux flavor world. Currently, DEFT is distributed as a live cd (taking up roughly 682mb of space).
DEFT is primarily developed by an Italian team, lead by Stefano Fraepietro. Other core team members include Salvo Tarantino, Davide Gabrini, Valerio Leomporra, Massimiliano Dal Cero and Alessandro Rossetti. DEFT is used by a variety of individuals, including professors, police and engineers.
Installation/Startup
DEFT is a LiveCD .iso so startup is as easy as configuring the BIOS, and inserting a disc with the burned iso. No virtualization software was needed, but first attempts at running this distribution involved the use of VirtualBox.
After booting up in a VirtualBox VM with 512 MB RAM allocated, it was soon realized that in order to get a true experience out of DEFT, being a forensic tool, it would be more appropriate to run on an existing machine running Windows.
To get it running:
- Burn a disc with the deft_6.1.iso file
- To run an .exe containing many of the forensic tools in the DEFT OS, put the disc into a running version of Windows
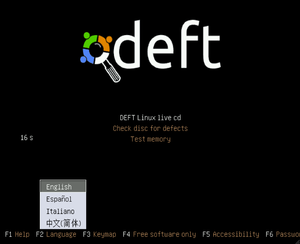
- To get to the DEFT startup menu (Figure 1), set the BIOS to boot from the CD/DVD drive primarily.
After choosing a language you can pick one of three options:
- DEFT Linux live cd
- Check disk for defects
- Test memory
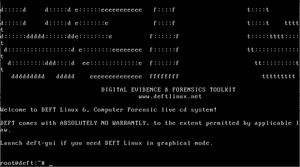
Check disk and test memory are just utilities for hardware checking, so the live cd option was chosen. DEFT goes through plenty of configuration operations and hardware scans to get the OS ready for use. Once this is all complete you are greeted by the main console screen of DEFT (Figure 2).
For a GUI Interface, type in 'deft-gui' into the console. Some of the applications in DEFT require the GUI to be used, such as Catfish or the Digital Forensic Framework (FDF).
Basic Operation
DEFT utilizes BASH or Bourne-again shell. Again, the shell functioned according to the norm that I have come to expect from debian-based distributions. I utilized ssh functionality from the shell, to ssh into my home server located at home.justincampbell.ca.
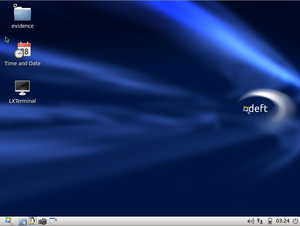
After working with basic bash/unix commands and shell scripts, I decided to work with the graphical user interface. I switched to graphical mode and began utilizing different applications and the desktop environment to perform “simple” tasks.
DEFT uses the LXDE windows manager (Figure 3). While I have been an avid Linux user since 2003, I have not used LXDE in any meaningful capacity before. LXDE has, thus far, proven to be a very simple user interface with very few issues.
The usage of DEFT was much like my experiences with KDE (and “Windows Aero”/the Windows environment). It seemed to have a similar menu and taskbar setup graphically, and was laid out much in the same manner of KDE and GNOME (to an extent). The graphical interface had “laggy” periods during read/write operations from disk; due to the operation system being a live cd.
Since DEFT is simply xubuntu with some specialty softwares most of my usage cases were related to the usage of particular programs related to forensics and other data ‘investigation’ tools.
One of the interesting applications from the suite is WINE, an emulator for windows applications. Due to the nature of the setup (Live CD), and the emulation nature of the application, applications run under WINE experienced a slower than “normal” execution time. The application I chose to emulate was PuTTY.
The application functioned properly, but noticeably slower that the counterpart ‘ssh’ commands from the linux shell.
Usage Evaluation
I found that this distribution was packed full of excellent programs for anyone wishing to carry out forensic analysis of a system and its contents.
Some of the tools, such as the various browser history and cache viewers were not much more than allowing a user to see a list, however for free software I did not expect anything too fancy. Other tools, like the Ophcrack Windows Password cracker seemed like it could be useful in many situations that would involve the use of DEFT.
This is the first distribution I have used where I found a graphical MountManager, which I found to be very helpful, and can see how it would be almost imperative for non-Linux users who do not have skills working at the command line.
All-in-all I can see how this distribution could be used well to serve its design purpose, and through use of the live CD can be used on a wide variety of machines anywhere, anytime. If I ever have need to carry out forensic analysis of digital evidence, I would most certainly consider using DEFT over some of its other commercial competitors.
Part 2
Software Packaging
Deft uses the apt-get command line tool that works with the Advanced Packaging Tool (APT). This tool provides a simple command line interface which can be used to update, remove, and install new packages as well as other features.
A list of installed packages can be obtained by running the dpkg utility:
>dpkg --get-selections
For the "front-end" interface, the Deft GUI uses the Synaptic Package Manager to allow you to browse for new packages, as well as update, install/remove, and allow you to view more information about a certain package. Packages are first archived with the tar utility and then compressed further with gzip.
To add packages to your system from the command line, you simply call
>apt-get install package-name
and apt-get will take care of the rest. To remove a package, use
>apt-get remove package-name
Packages are downloaded from repositories (directories or disks with an index) that are sourced in APT's sources.list config file.
Major Package Versions
Initialization
When the computer is started, its BIOS boots grub. Grub goes on to load the kernel and gives control to the init process.
Part 3
References
http://www.deftlinux.net/ DEFT Linux Homepage
http://www.deftlinux.net/deft-manual/ DEFT User Guide
http://www.gzip.org/#faq16 Gzip FAQ's
http://linux.die.net/man/8/apt-get apt-get Manual page
http://www.linuxplanet.com/linuxplanet/tutorials/7033/1 Upstart Tutorial