COMP 3000 2011 Report: CAINE: Difference between revisions
| Line 89: | Line 89: | ||
===Autopsy=== | ===Autopsy=== | ||
The "Autopsy 2.24" opened a | The "Autopsy 2.24" opened a program that launches in a browser window. This software allows for a user to create a new case or open a previously created one. '''Figure 5''' [[File:Autopsy.png|thumb|left| '''Figure 5''' The start of the Autopsy software.]] | ||
Upon creating a new case, the software asks for the case name, a short description, and a list of all the investigators that are assigned to this case. Once this has all been filled out, the program then asks for a host to be created. This host is the computer that is currently under investigation. The program then asks for the name of the host computer and a short description. Also, optionally, it asks for a specified timezone, timeskew adjustment (to compensate for how much or little the computer is off from another computer's time), and a hashtable for known good and bad files. Once this is complete, the program asks for an image file, which is interpreted as a filepath. Then it asks if this file path points to a disk or partition, and then finally how to extract the files, either by moving, copying, or simply linking to them. | |||
At this point, I did not have an image file on hand to investigate, so I could not delve further into this program. | |||
==Usage Evaluation== | ==Usage Evaluation== | ||
Revision as of 19:48, 18 October 2011
Part 1
Background
CAINE, which stands for Computer Aided INvestigative Environment, is a Linux environment whose main purpose is to provide specific investigative and reporting tools that would prove useful to a forensic scientists.<ref name = "CAINE">CAINE-Live Website (Last accessed October 19, 2011).</ref> This Linux environment was originally created in Italy and is currently being managed by Mr. Nanni Bassetti (Website in Italian).
Something to consider before diving into what CAINE is used for is to get a quick understanding about the four step process model put in place by the U.S Department of Justice with regards to digital forensics.<ref name = "DigiForen">Digital Forensics - The Enhanced Digital Investigation Process Model (Last accessed October 14th, 2011).</ref>
The four stages of digital forensics:<ref name = "DigiForen"/>
- Collection deals with evidence finding, recognition, collection, and some early documentation with details about the evidence.
- Examination has the scientist sifting through the already collected evidence with different software. The goal is to find out where the evidence came from and if it is significant. It also may reveal previously unknown information about the piece of evidence with in-depth examination.
- Analysis happens after Examination has deemed a piece of evidence significant enough. By piecing together information gained through the Examination stage, the scientist will decide just how relevant the evidence is to the current case.
- Reporting, the final stage, is writing a simple report touching on the examination process and giving a detailed look at all the relevant information gathered through Examination and Analysis that will hopefully help the case in some way.
The design goals that CAINE strives to achieve are as follows:<ref name = "CAINE"/>
- A diverse environment that gives the flexibility and all the tools necessary to the forensic scientist during all four stages of the digital forensics.
- A user-friendly GUI.
- A tool which provided a simple, semi-automatic solution for reporting.
Obtaining CAINE is quite simple. The main website hosts the under 700MB .ISO file directly. The direct download link to CAINE can be found here. There is also an 865MB file that is available for netbooks as well. It can be found here.
Finally, CAINE was created with pieces from Ubuntu 10.04 and Remastersys created by Tony Brijeski<ref name = "CAINEFAQ">CAINE FAQs (Last accessed October 17th, 2011)</ref>
Installation/Startup
Initialization
Upon starting up CAINE for the very first time. Something to note is that the installation doesn't actually start upon first boot-up. Since CAINE's .ISO file is a Live CD, it has the full operating system with pre-configured software and settings<ref name = "LiveCD">The Magic of Live CDs (Last accessed October 17th, 2011).</ref>. For the sake of seeing how the installation process works, though, I will go through and ensure that CAINE is actually installed the HDD.
The software that was used to virtualize CAINE was VMWare Workstation, specifically version 7.1.4 build-385536. [Figure 1]

The specifications of the virtual machine are as follows:
- Typical install (Creates a Workstation 6.5-7.x virtual machine)
- Selected the Caine 2.5 .ISO file.
- Selected a Linux operating system with type "Other Linux 2.6.x kernel".
- Allocated 20GB for the virtual machine and 512MB of RAM.
CAINE booted up with no initial problems with a boot screen full of options. [Figure 2]
The options include:
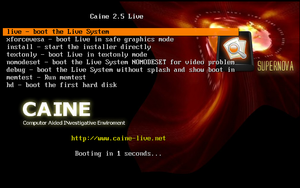
- Booting the Live System (which is chosen if no action is taken in 10 seconds).
Figure 3 CAINE's Live-CD desktop. The time is currently incorrect. - Low-graphics mode for lower-end machines.
- Command to start the full-install right away.
- Text only mode.
- Video diagnostics command.
- Debug mode.
- Memory diagnostics command.
- Boot from the first HDD.
NOTE: At this point, do not attempt to restart the virtual machine. The system will hang and you will have no choice but to force close the virtual machine and re-open.
After either selecting the Live Boot or waiting for 10 seconds, the desktop will be displayed. [Figure 3]
Installation
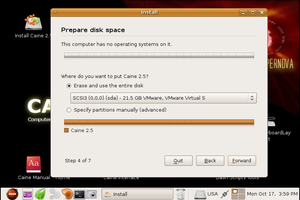
Note: All choices made in the test install will be written in parantheses.
After clicking on the Install CAINE 2.5 icon, the user is given the option of selecting a language (English). The installation then initializes the clock to some server's clock, and asks for the user to select the time zone by region (Canada) and Time Zone (Canada Toronto). Afterwards, the user is prompted to selected a keyboard, with the suggested option being USA (USA). Next, the user is prompted to specify a partition in which to install Caine 2.5 on (Erase and use the entire disk) [Figure 4]. The user is then prompted to enter their name, username, password, and the name of the computer. Once this is complete, the user is shown a review of all the choices they have made with a final message stating that all these choices will be applied to the disk upon clicking "Install".
The CAINE operating system will now begin installing to the HDD. Once the installation is complete, the user will be prompted to either restart or continue with manual configurations. Now the virtual machine can be properly restarted without needing to force quit the virtual machine. Upon restarting, the user is asked to choose either the operating system, or the memory diagnostics tool. Something to note is that the operating system that is available isn't called "CAINE", it says "Ubuntu, with Linux 2.6.32-33-generic". This most likely comes from the fact that CAINE was born from Ubuntu and most likely shares a lot of its kernal.
Basic Operation
Being a beginner when it comes to all forms of forensics, whether actual work or documentation, I will do my best to give an appropriate overview of CAINE.
Since CAINE was intended specifically for people who work in the digital forensics field, I started looking around the OS for some of the software the developer said could help in all stages of digital forensics.
Autopsy
The "Autopsy 2.24" opened a program that launches in a browser window. This software allows for a user to create a new case or open a previously created one. Figure 5
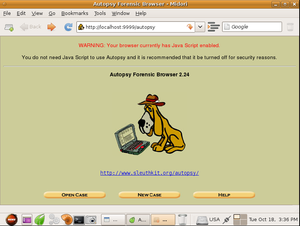
Upon creating a new case, the software asks for the case name, a short description, and a list of all the investigators that are assigned to this case. Once this has all been filled out, the program then asks for a host to be created. This host is the computer that is currently under investigation. The program then asks for the name of the host computer and a short description. Also, optionally, it asks for a specified timezone, timeskew adjustment (to compensate for how much or little the computer is off from another computer's time), and a hashtable for known good and bad files. Once this is complete, the program asks for an image file, which is interpreted as a filepath. Then it asks if this file path points to a disk or partition, and then finally how to extract the files, either by moving, copying, or simply linking to them.
At this point, I did not have an image file on hand to investigate, so I could not delve further into this program.
Usage Evaluation
References
<references />