COMP 3000 2011 Report: QuebeOS beta 2: Difference between revisions
| (3 intermediate revisions by the same user not shown) | |||
| Line 3: | Line 3: | ||
===Background=== | ===Background=== | ||
[[File:droppedImage.png|200px|thumb|right|A visual representation of the security system used by Quebes]] | [[File:droppedImage.png|200px|thumb|right|A visual representation of the security system used by Quebes]] | ||
[http://qubes-os.org/ Quebes] is a very new Operating System based off the Linux OS combined with the Xen Hypervisor and X Windows System GUI aimed primarily at people dealing with confidential information but also anybody who is concerned about their computer security. The first beta was released on Apr 11, 2011 and the 2nd beta was released on Sep 19, 2011. It is actively being developed by [http://invisiblethingslab.com/ Invisible Things Lab] and it can be downloaded from [http://wiki.qubes-os.org/trac/wiki/InstallationGuide here] weighing in at a hefty 1.59gb for the | [http://qubes-os.org/ Quebes] is a very new Operating System based off the Linux OS combined with the Xen Hypervisor and X Windows System GUI aimed primarily at people dealing with confidential information but also anybody who is concerned about their computer security. The first beta was released on Apr 11, 2011 and the 2nd beta was released on Sep 19, 2011. It is actively being developed by [http://invisiblethingslab.com/ Invisible Things Lab] and it can be downloaded from [http://wiki.qubes-os.org/trac/wiki/InstallationGuide here] weighing in at a hefty 1.59gb for the install dvd. | ||
This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. | This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. | ||
==='Hardware Requirements=== | |||
'''Minimum:''' | '''Minimum:''' | ||
4GB of RAM | 4GB of RAM | ||
64-bit Intel or AMD processor (x86_64 aka x64 aka AMD64) | 64-bit Intel or AMD processor (x86_64 aka x64 aka AMD64) | ||
Intel GPU strongly preferred (if you have Nvidia GPU, prepare for some troubleshooting; we haven't tested ATI hardware) | |||
10GB of disk (Note that it is possible to install Qubes on an external USB disk, so that you can try it without sacrificing your current system. Mind, however, that USB disks are usually SLOW!) | Intel GPU strongly preferred (if you have Nvidia GPU, prepare for some troubleshooting; we haven't tested ATI hardware) | ||
Fat SSD disk strongly recommended | |||
10GB of disk (Note that it is possible to install Qubes on an external USB disk, so that you can try it without sacrificing your current system. Mind, however, that USB disks are usually SLOW!) | |||
Fat SSD disk strongly recommended | |||
'''Additional criteria''' | '''Additional criteria''' | ||
Intel VT-d or AMD IOMMU technology (this is needed for effective isolation of your network VMs) | Intel VT-d or AMD IOMMU technology (this is needed for effective isolation of your network VMs) | ||
If you don't meet the additional criteria, you can still install and use Qubes. It still offers significant security improvement over traditional OSes, because things such as GUI isolation, or kernel protection do not require special hardware. | If you don't meet the additional criteria, you can still install and use Qubes. It still offers significant security improvement over traditional OSes, because things such as GUI isolation, or kernel protection do not require special hardware. | ||
Note: We don't recommend installing Qubes in a virtual machine! Note: There is a problem with supporting keyboard and mouse on Mac, and so Mac hardware is currently unsupported (patches welcomed!) | Note: We don't recommend installing Qubes in a virtual machine! Note: There is a problem with supporting keyboard and mouse on Mac, and so Mac hardware is currently unsupported (patches welcomed!) | ||
Latest revision as of 23:02, 16 October 2011
Part 1
Background
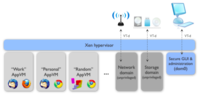
Quebes is a very new Operating System based off the Linux OS combined with the Xen Hypervisor and X Windows System GUI aimed primarily at people dealing with confidential information but also anybody who is concerned about their computer security. The first beta was released on Apr 11, 2011 and the 2nd beta was released on Sep 19, 2011. It is actively being developed by Invisible Things Lab and it can be downloaded from here weighing in at a hefty 1.59gb for the install dvd.
This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this, it actually runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system.
'Hardware Requirements
Minimum:
4GB of RAM 64-bit Intel or AMD processor (x86_64 aka x64 aka AMD64)
Intel GPU strongly preferred (if you have Nvidia GPU, prepare for some troubleshooting; we haven't tested ATI hardware)
10GB of disk (Note that it is possible to install Qubes on an external USB disk, so that you can try it without sacrificing your current system. Mind, however, that USB disks are usually SLOW!)
Fat SSD disk strongly recommended
Additional criteria
Intel VT-d or AMD IOMMU technology (this is needed for effective isolation of your network VMs)
If you don't meet the additional criteria, you can still install and use Qubes. It still offers significant security improvement over traditional OSes, because things such as GUI isolation, or kernel protection do not require special hardware.
Note: We don't recommend installing Qubes in a virtual machine! Note: There is a problem with supporting keyboard and mouse on Mac, and so Mac hardware is currently unsupported (patches welcomed!)