COMP 3000 2011 Report: Qubes beta 2: Difference between revisions
| (One intermediate revision by the same user not shown) | |||
| Line 7: | Line 7: | ||
The first beta was released on Apr 11, 2011, and the 2nd beta was released on Sep 19, 2011. It is actively being developed by [http://invisiblethingslab.com/ Invisible Things Lab] and it can be downloaded from [http://wiki.qubes-os.org/trac/wiki/InstallationGuide here]. The install dvd is quite big at 1.59gb for the install DVD. In comparison, Ubuntu and most other Linux distributions will still fit on a 700mb CD. | The first beta was released on Apr 11, 2011, and the 2nd beta was released on Sep 19, 2011. It is actively being developed by [http://invisiblethingslab.com/ Invisible Things Lab] and it can be downloaded from [http://wiki.qubes-os.org/trac/wiki/InstallationGuide here]. The install dvd is quite big at 1.59gb for the install DVD. In comparison, Ubuntu and most other Linux distributions will still fit on a 700mb CD. | ||
This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this; it runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. From my research it does not appear that there are any other operating systems available that have used this technique. | This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this; it runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system. | ||
From my research it does not appear that there are any other operating systems available that have used this technique. There are many users of the Xen software in combination with Linux, but it is always used to run multiple Operating Systems simultaneously. This approach to security is significantly more secure (between the different OSs) than the Qubes approach (between the different app VMs) but at the expense of a multitude of CPU power. | |||
One of the truly revolutionary parts of this platform is the way that the GUI integrates the multiple VMs in order to make it as seamless as possible for the user to manage. The other majorly revolutionary part of this platform is the fact that it sandboxes parts of the system like networking (by isolating them in a VM) for extra security. | One of the truly revolutionary parts of this platform is the way that the GUI integrates the multiple VMs in order to make it as seamless as possible for the user to manage. The other majorly revolutionary part of this platform is the fact that it sandboxes parts of the system like networking (by isolating them in a VM) for extra security. | ||
| Line 78: | Line 80: | ||
Overall this is great for people who really need the security and stability that this architecture provides, but the requirements are a little bit too ridiculous (and it might be a little unnecessary for ordinary users) to become truly mainstream at the moment. In my VM with 3.2gb of ram dedicated I was only able to run the basic VMs. While 4gb and a 64bit processor is standard in computers purchased in the past year, the reality is that right now, most computers out there do not meet these requirements. | Overall this is great for people who really need the security and stability that this architecture provides, but the requirements are a little bit too ridiculous (and it might be a little unnecessary for ordinary users) to become truly mainstream at the moment. In my VM with 3.2gb of ram dedicated I was only able to run the basic VMs. While 4gb and a 64bit processor is standard in computers purchased in the past year, the reality is that right now, most computers out there do not meet these requirements. | ||
As I mentioned I ran Qubes in a VM, obviously this is not a fair test since it runs VMs inside of itself and my system is not powerful enough to fully utilize the system like this. I did it that way because I had no choice when it refused to boot natively on any of my computers. I still think it has been enough experience to learn what I needed to learn in order to write this report. | |||
===References=== | ===References=== | ||
<references/> | <references/> | ||
Latest revision as of 17:49, 20 December 2011
Part 1
Background
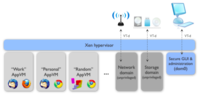
Quebes is a very new Operating System based off of Fedora Linux OS and the Xen Hypervisor. It is aimed primarily at people dealing with confidential information, but could it be used by anybody who is concerned about their computer security.
The first beta was released on Apr 11, 2011, and the 2nd beta was released on Sep 19, 2011. It is actively being developed by Invisible Things Lab and it can be downloaded from here. The install dvd is quite big at 1.59gb for the install DVD. In comparison, Ubuntu and most other Linux distributions will still fit on a 700mb CD.
This OS is designed with the primary goal of being secure. It employs a highly unique and interesting technique to achieve this; it runs some of the system components in a virtual machine and it runs user applications in separate user defined virtual machines. This theoretically isolates applications and their memory contents. This makes it such that if one application misbehaves or is maliciously exploited it is unlikely to have an effect on other applications in a separate VM or the running system.
From my research it does not appear that there are any other operating systems available that have used this technique. There are many users of the Xen software in combination with Linux, but it is always used to run multiple Operating Systems simultaneously. This approach to security is significantly more secure (between the different OSs) than the Qubes approach (between the different app VMs) but at the expense of a multitude of CPU power.
One of the truly revolutionary parts of this platform is the way that the GUI integrates the multiple VMs in order to make it as seamless as possible for the user to manage. The other majorly revolutionary part of this platform is the fact that it sandboxes parts of the system like networking (by isolating them in a VM) for extra security.
Hardware Requirements<ref>http://wiki.qubes-os.org/trac/wiki/InstallationGuide</ref>
Minimum:
4GB of RAM 64-bit Intel or AMD processor (x86_64 aka x64 aka AMD64)
Intel GPU strongly preferred (if you have Nvidia GPU, prepare for some troubleshooting; we haven't tested ATI hardware)
10GB of disk (Note that it is possible to install Qubes on an external USB disk, so that you can try it without sacrificing your current system. Mind, however, that USB disks are usually SLOW!)
Fat SSD disk strongly recommended
Additional criteria
Intel VT-d or AMD IOMMU technology (this is needed for effective isolation of your network VMs)
If you don't meet the additional criteria, you can still install and use Qubes. It still offers significant security improvement over traditional OSes, because things such as GUI isolation, or kernel protection do not require special hardware.
Note: We don't recommend installing Qubes in a virtual machine! Note: There is a problem with supporting keyboard and mouse on Mac, and so Mac hardware is currently unsupported (patches welcomed!)
Installation/Startup
Install is pretty standard and straightforward compared with other OSs and Linux distros I am installing on a 2011 MacBook pro (which I know is unsupported, but let's see how it goes…) unfortunately I am going to be installing to an external hard drive so I will not be able to give a true performance evaluation.
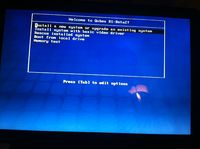
I ran into my first issue very quickly which was that I did not read there release notes for beta 2 and I discovered that the installer does not support my macbook pro keyboard but this was quickly remedied by plugging in a USB keyboard. I decided to skip the disk check and then I was asked to partion my drive and set a time zone. I chose to encrypt my hard drive because it would feel a little hypocritical not to with such a secure OS.
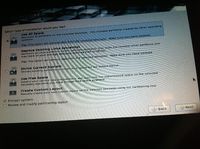
After that the install failed, let this be a lesson to you to check your disk if you want to potentially save some time. I redownloaded the imagine and went through the installation again, now after completing the installation my mac was unable to boot from the USB hard drive, so I gave the usb hard drive a try on a PC as well as through REefIt mac software and it wouldn't boot. So I gave a native installation a try, I wiped my bootcamp partition off my macbook and I installed Qubes in its place. To my disappointment it still would not boot and REefIt could see it but it would just say "No Operating System Present, Insert Bootable Disk and Press Enter To Continue".
So I gave up and I installed Qubes in a VM which is incapable of showing its true power and is not recommended but I was left with no options to get this OS up and running. I used VMWare Fusion to run it.
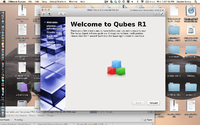
Upon the first boot I was greeted with a nice welcome screen that walked me through creating a user account and asked me how I wanted to manage my VM bottles. It gives you 3 options at this point, you can have it automatically create the default app VMs (which is what most basic users want), you could manually specify the app VMs (which could be useful for tweaking the system for extra security at the expense of speed) and then there's the option not to create any VMs which is not recommended.
The default option creates a dom0 VM that is used system operations that require special access, a networking VM, a separate VM for other system applications and one for user applications. By manually defining more VMs you could also create separate VMs for work apps, home apps, apps that deal with confidential information, etc. If you select to not create any VMs then the system is essentially a modified Linux distro, and it takes away the most of the advantage of this OS, it will only have the dom0 virtual machine and everything runs on that.
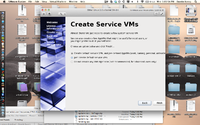
After these simple steps you will end up at the standard KDE login screen.
Basic Operation
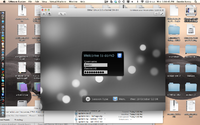
Qubes runs a seemingly unmodified version of KDE graphical environment but unfortunately it is stripped down and contains only a few of the nice goodies that usually come along with that. The only difference that can be noted from a standard linux desktop running KDE is that it has an extra icon in the taskbar which can be used for managing app VMs. This app gives you all the options you need to manage your different VMs, you first name the VM, then you can choose whether or not this VM has access to the network, then you can transfer over to the advanced tab and set the maximum size of the VM and how much ram and cpu resources you would like to devote to it.
The way the system manages interaction between the virtual machines is the key of this distribution. All applications have their files stored in the .img file of the VM which they are part of. Applications have readonly access to the image filesystem and store their files directly on the filesystem.
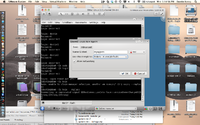
The intended usage for this distribution is general productivity in a secure manner, so I decided to try installing some applications and putting them in different VMs in order to see how the VMs look to the user and how it deals with package management and updates inside the VMs.
Since this system is baed on fedora, it uses RPM packages and has the default package manager 'yum' with a kde frontend. It worked flawlessly, I installed a web browser and the open office suite and attempted to separate them into multiple VMs. Unfortunately this was too much for my system to handle running it in a VM and it politely displayed the message 'failed to start custom VM' and open office refused to open until I moved it back into the default VM. This is perfectly acceptable though given that my system just meets the requirements to run this OS natively so some hiccups are to be expected.
In terms of security, there are clear advantages to this approach to managing applications in this manner. It makes it theoretically very difficult for a malicious 3rd party to exploit an application and gain root access to the system. There is definitely a big performance hit that occurs when running so many VMs at the same time though.
Everything seems very sluggish when compared to other linux distributions like Ubuntu running in the same environment. Like many modern operating systems, the scheduler in Qubes appears to prioritze the things that people notice. For example, opening a program might take 10-20 seconds from clicking on it to start actually seeing the program open, but things like highlighting, moving the cursor around, etc did not lag at all which makes the user feel better about the performance.
Usage Evaluation
With the goal being security, this distribution definitely accomplishes that in a way that provides different levels of security depending on the computing knowledge of the user or administrator. It appears to be aimed at advanced computer users especially given that the website makes little effort to explain the basic concepts behind a VM which the whole OS is based on. From my experience this distribution need not only be aimed at advanced users because it provides a much higher level of security than a normal OS in some fields and unless the user wants to manage it, it is almost completely transparent.
Note: This is beta software and it might just not be aimed at regular users for this reason.
From the start the system will setup VMs for the user, mainly the system VMs; it creates one for the networking components of the OS and one for the GUI, and then it also creates a default user application VM. Then if the user is advanced enough and understands the advantages they can manually separate apps into the 2 VMs with ease.
Overall this is great for people who really need the security and stability that this architecture provides, but the requirements are a little bit too ridiculous (and it might be a little unnecessary for ordinary users) to become truly mainstream at the moment. In my VM with 3.2gb of ram dedicated I was only able to run the basic VMs. While 4gb and a 64bit processor is standard in computers purchased in the past year, the reality is that right now, most computers out there do not meet these requirements.
As I mentioned I ran Qubes in a VM, obviously this is not a fair test since it runs VMs inside of itself and my system is not powerful enough to fully utilize the system like this. I did it that way because I had no choice when it refused to boot natively on any of my computers. I still think it has been enough experience to learn what I needed to learn in order to write this report.
References
<references/>